| Age | Commit message (Collapse) | Author |
|---|
|
Add the ability for users to change their password from their user settings, without requiring them to use the reset password workflow. User's are required to create a elevated session in order to change their password. Users may not change their password to their current password. The user's current password is required for the password change. Users must follow any established password policies. Administrators are able to turn this feature off.
Closes #3548
|
|
Signed-off-by: Amir Zarrinkafsh <nightah@me.com>
|
|
Signed-off-by: Amir Zarrinkafsh <nightah@me.com>
|
|
This adds several tests to several areas as per standard security practices, specifically adding a lot of testing to WebAuthn.
|
|
Add tests and adjust tests and code as appropriate. This also ensures we have thorough coverage of the code.
Signed-off-by: James Elliott <james-d-elliott@users.noreply.github.com>
|
|
Signed-off-by: James Elliott <james-d-elliott@users.noreply.github.com>
|
|
This implements some HEAD method handlers for various static resources and the /api/health endpoint.
|
|
This allows users to customize the authz endpoints.
Closes #2753, Fixes #3716
Co-authored-by: Amir Zarrinkafsh <nightah@me.com>
|
|
* test(suites): load environment into suites
* test(suites): default setup suite
* test(suites): create base suite
* test(suites): fix nil ptr
* test(suites): add logging
* test: fix missing devworkflow path
* refactor: apply suggestions
* refactor: log
* fix: dev workflow requires env file to trigger vite hmr
* fix(suites): fix dynamic configuration in dev workflow for all proxies
* refactor: apply final suggestions
* fix: pass log level to suites
* fix(suites): include pathprefix to prevent react router basename issues
* fix: missing setup logging calls
* fix: gate suite setup funcs
* test: fix lint
* test: fix tmp dir
* fix(suites): fix gitignore of .env.development with vite hmr
Co-authored-by: Amir Zarrinkafsh <nightah@me.com>
|
|
This adds support to configure multiple session cookie domains.
Closes #1198
Co-authored-by: James Elliott <james-d-elliott@users.noreply.github.com>
Co-authored-by: Amir Zarrinkafsh <nightah@me.com>
|
|
|
|
This PR checks the authentication state of the Authelia portal on either a focus event or 1-second timer and if a state change has occurred will redirect accordingly.
Closes #3000.
Co-authored-by: Amir Zarrinkafsh <nightah@me.com>
|
|
|
|
Adds ability to record metrics and gather them for Prometheus.
|
|
* test: add redis restart test back to traefik2 suite
* refactor(suites): mustpress -> mustinput for totp
* refactor(suites): rename suites for test ordering
|
|
This implements Webauthn. Old devices can be used to authenticate via the appid compatibility layer which should be automatic. New devices will be registered via Webauthn, and devices which do not support FIDO2 will no longer be able to be registered. At this time it does not fully support multiple devices (backend does, frontend doesn't allow registration of additional devices). Does not support passwordless.
|
|
|
|
Prevents the TOTP user config from being requested when the user has not registered or is already authenticated 2FA.
|
|
Was deprecated in 1.16 and has more performant options available.
|
|
Allow users to configure the TOTP Algorithm and Digits. This should be used with caution as many TOTP applications do not support it. Some will also fail to notify the user that there is an issue. i.e. if the algorithm in the QR code is sha512, they continue to generate one time passwords with sha1. In addition this drastically refactors TOTP in general to be more user friendly by not forcing them to register a new device if the administrator changes the period (or algorithm).
Fixes #1226.
|
|
This adds an AES-GCM 256bit encryption layer for storage for sensitive items. This is only TOTP secrets for the time being but this may be expanded later. This will require a configuration change as per https://www.authelia.com/docs/configuration/migration.html#4330.
Closes #682
|
|
This is a massive overhaul to the SQL Storage for Authelia. It facilitates a whole heap of utility commands to help manage the database, primary keys, ensures all database requests use a context for cancellations, and paves the way for a few other PR's which improve the database.
Fixes #1337
|
|
* refactor(suites): replace selenium with go-rod
This change replaces [tebeka/selenium](https://github.com/tebeka/selenium) with [go-rod](https://github.com/go-rod/rod).
We no longer have a chromedriver/external driver dependency to utilise Selenium as we instead utilise the Chrome Dev Protocol to communicate with the browser.
Rod [documents](https://go-rod.github.io/#/why-rod) benefits of choosing the library as opposed to the available alternatives.
|
|
* build: include major in go.mod module directive
* fix: xflags
* revert: cobra changes
* fix: mock doc
|
|
* fix(handlers,web): user is now redirected when authenticated
Fix: #1788
* remove dead code and fix ci issues
* fix infinite loop in frontend
* fix issue with integration tests
* handle bot recommendation
* fix integration test & add dot to comment
* fix last integration test
* Update api/openapi.yml
Co-authored-by: James Elliott <james-d-elliott@users.noreply.github.com>
* Update web/src/services/SafeRedirection.ts
Co-authored-by: Amir Zarrinkafsh <nightah@me.com>
* Update web/src/services/SafeRedirection.ts
Co-authored-by: Amir Zarrinkafsh <nightah@me.com>
* Update api/openapi.yml
* Update openapi.yml
* refactor: valid -> safe
* refactor: adjust merge conflicts
* Apply suggestions from code review
Co-authored-by: James Elliott <james-d-elliott@users.noreply.github.com>
* fix: adjust test return messaging
Co-authored-by: James Elliott <james-d-elliott@users.noreply.github.com>
Co-authored-by: Amir Zarrinkafsh <nightah@me.com>
|
|
This changes the way XML HTTP requests are handled on the verify endpoint so that they are redirected using a 401 instead of a 302/303.
|
|
When a request occurs, if the browser is not performing a HTTP GET/HEAD request, the 302 status code is not valid. This commit resolves this. MDN: https://developer.mozilla.org/en-US/docs/Web/HTTP/Status/302.
|
|
|
|
This PR changes the suites tests so if go test -short is used, they are skipped per go standards and a message is displayed. Additionally removed some redundant types from suite_high_availability_test.go and adjusted a warning about a nil req var.
|
|
* adjust session refresh to always occur (for disabled users)
* feat: adds filtering option for Request Method in ACL's
* simplify flow of internal/authorization/authorizer.go's methods
* implement query string checking
* utilize authorizer.Object fully
* make matchers uniform
* add tests
* add missing request methods
* add frontend enhancements to handle request method
* add request method to 1FA Handler Suite
* add internal ACL representations (preparsing)
* expand on access_control next
* add docs
* remove unnecessary slice for network names and instead just use a plain string
* add warning for ineffectual bypass policy (due to subjects)
* add user/group wildcard support
* fix(authorization): allow subject rules to match anonymous users
* feat(api): add new params
* docs(api): wording adjustments
* test: add request method into testing and proxy docs
* test: add several checks and refactor schema validation for ACL
* test: add integration test for methods acl
* refactor: apply suggestions from code review
* docs(authorization): update description
|
|
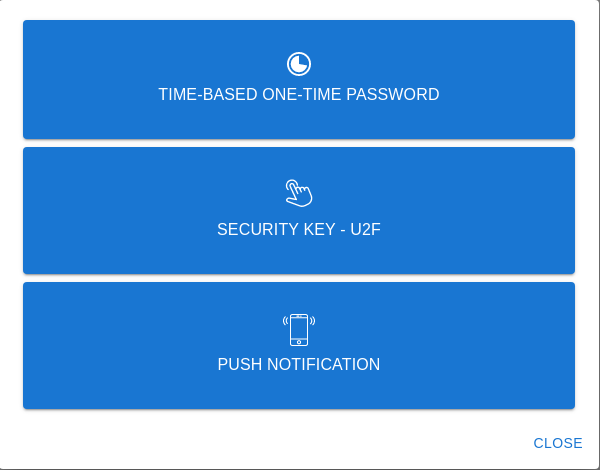
* refactor(web): improve 2fa enrollment process
This PR will change some of the wording and colours for the 2FA processes in order to provide more clarity and address some accessibility issues for end users.
The following is a summary of the changes:
* One-Time Password ⭢ Time-based One-Time Password
* Security Key ⭢ Security Key - U2F
* QRCode ⭢ QR Code

* `Not registered yet?` text to display `Lost device?` if a user has already registered a device of said type
* Change button and text colour in e-mails that Authelia generates
* Change Authelia email footer to be more security conscious
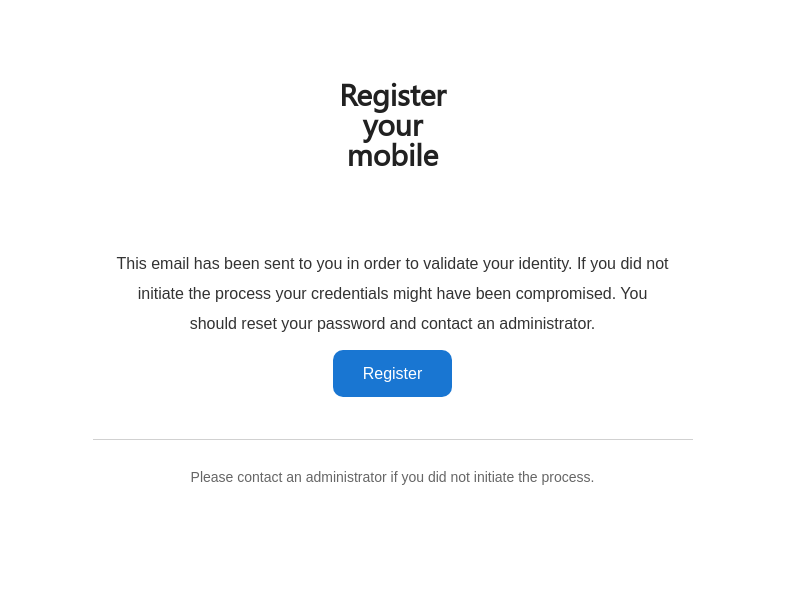
The docs have also been updated to clarify the 2fa device enrollment limitation which only allows users to register one of each device type concurrently.
Closes #1560.
|
|
Add a suite for testing the PathPrefix feature implemented earlier to serve authelia under a multi-purpose domain.
Co-authored-by: Clément Michaud <clement.michaud34@gmail.com>
|
|
* [CI] Add godot linter
* Implement godot recommendations
|
|
* added regulation validator
* made regulations find_time and ban_time values duration notation strings
* added DefaultRegulationConfiguration for the validator
* made session expiration and inactivity values duration notation strings
* TOTP period does not need to be converted because adjustment should be discouraged
* moved TOTP defaults to DefaultTOTPConfiguration and removed the consts
* arranged the root config validator in configuration file order
* adjusted tests for the changes
* moved duration notation docs to root of configuration
* added references to duration notation where applicable
* project wide gofmt and goimports:
* run gofmt
* run goimports -local github.com/authelia/authelia -w on all files
* Make jwt_secret error uniform and add tests
* now at 100% coverage for internal/configuration/validator/configuration.go
|
|
(#611)
* Redirect to default URL after 1FA when default policy is one_factor.
User is now redirected to the default redirection URL after 1FA if
the default policy is set to one_factor and there is no target URL
or if the target URL is unsafe.
Also, if the default policy is set to one_factor and the user is already
authenticated, if she visits the login portal, the 'already authenticated'
view is displayed with a logout button.
This fixes #581.
* Update users.yml
* Fix permissions issue causing suite test failure
|
|
* Encode URL set to rd parameter.
URL encoding that parameter solves PR #476.
Some URL parameters set during redirection were magically disappearing
after the redirection due to the authentication process. By using URL encoding,
those parameters should not be stripped anymore.
* Fix integration tests.
|
|
* Build docker image upfront in CI and use it in integration tests.
Previously, the development workflow was broken because the container
generated from Dockerfile.CI was used in dev environments but the binary
was not pre-built as it is on buildkite. I propose to just remove that
image and use the "to be published" image instead in integration tests.
This will have several advantages:
- Fix the dev workflow.
- Remove CI arch from authelia-scripts build command
- Optimize CI time in buildkite since we'll cache a way small artifact
- We don't build authelia more than once for earch arch.
* Fix suites and only build ARM images on master or tagged commits
* Optimise pipeline dependencies and Kubernetes suite to utilise cache
* Run unit tests and docker image build in parallel.
* Fix suite trying to write on read only fs.
Co-authored-by: Amir Zarrinkafsh <nightah@me.com>
|
|
Also fix references from config.yml to configuration.yml
|
|
Providing a GA tracking ID allows administrators to analyze
how the portal is used by their users in large environments,
i.e., with many users.
This will make even more sense when we have users and admins
management interfaces.
|
|
|
|
|
|
https://github.com/golang-standards/project-layout
|
